As web applications grow in complexity, managing user permissions becomes a critical aspect of software development. Role-Based Access Control (RBAC) is a widely adopted methodology for controlling access to resources based on a user’s role within an organization. Implementing RBAC in full stack applications ensures robust security while streamlining user management processes. For those looking to gain expertise in this area, enrolling in a full stack developer course provides the foundational knowledge necessary to design and implement such features effectively.
Understanding Role-Based Access Control (RBAC)
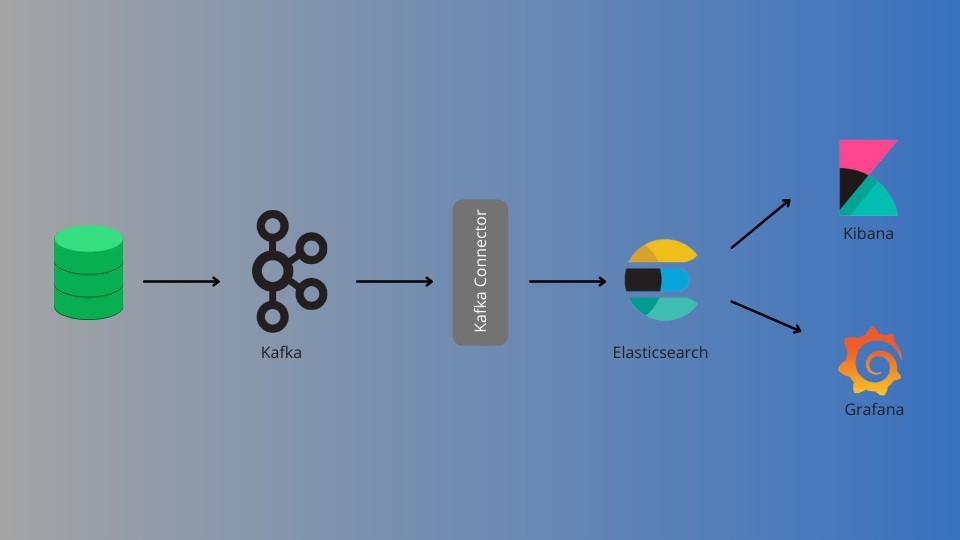
RBAC assigns permissions to users based on predefined roles, simplifying the management of user access in applications. Instead of granting individual permissions to each user, developers can create roles—such as admin, editor, or viewer—and assign users to these roles. This approach reduces redundancy, minimizes errors, and improves scalability.
In a full stack application, RBAC implementation spans both the frontend and backend. The frontend ensures that users see only the functionalities available to their role, while the backend enforces access restrictions on sensitive resources. This division of responsibilities demands proficiency in full stack development, which can be honed through structured learning pathways.
Designing an RBAC System
Before implementing RBAC, it’s crucial to design a system tailored to your application’s requirements. Start by identifying the roles and permissions necessary for your platform. For instance, a blogging platform might include roles such as writer, editor, and admin, each with distinct capabilities.
The next step is creating a permissions matrix that maps roles to specific actions or resources. This matrix acts as a blueprint for configuring RBAC in your database and application logic. With this groundwork, developers can proceed to implement role-based controls on both the client and server sides.
For aspiring developers based in India, pursuing a full stack course in Hyderabad can provide hands-on experience in designing scalable systems, including advanced features like RBAC. Such programs often cover essential backend frameworks and frontend technologies that are vital for this process.
Implementing RBAC on the Backend
The backend plays a pivotal role in RBAC implementation, as it enforces access controls and manages authentication. A typical backend stack for RBAC includes:
- Database Configuration: Define tables for users, roles, and permissions. These tables should be relationally linked to streamline access checks. For example, a “user_roles” table can associate users with their assigned roles.
- Middleware for Authorization: Middleware functions intercept incoming requests and verify if the user has the required permissions to access a resource. This logic is often built using frameworks like Express.js for Node.js or Django for Python.
- Token-Based Authentication: To enhance security, use tokens such as JSON Web Tokens (JWT) to store user role information. Each request can then be validated against the user’s permissions encoded in the token.
Mastering these backend techniques requires a solid understanding of server-side development. For those starting their journey, a full stack developer course provides structured guidance on building secure and scalable backend systems.
Implementing RBAC on the Frontend
The frontend complements the backend by ensuring a seamless user experience. In RBAC, the frontend’s role is to display user-specific content and disable or hide restricted actions. This requires careful integration with the backend to fetch role-specific data and enforce visual restrictions.
Popular frontend libraries like React, Angular, and Vue.js are often used to build RBAC-compatible user interfaces. Here’s how you can integrate RBAC into the frontend:
- Dynamic Rendering: Use conditional rendering to display components or actions based on the user’s role. For instance, an “Edit” button might only be visible to users with editor or admin privileges.
- State Management: Implement state management solutions like Redux or Vuex to store and manage user roles throughout the application.
- Error Handling: Provide user-friendly feedback for unauthorized actions. For example, show a message like “You do not have permission to perform this action” when a user attempts to access restricted features.
Such frontend integration techniques are extensively covered in practical training sessions offered by a full stack course in Hyderabad, where students work on real-world projects to develop their skills.
Challenges in Implementing RBAC
While RBAC simplifies access management, implementing it in a full stack application can be challenging. Common hurdles include:
- Role Explosion: As the number of roles and permissions increases, maintaining the system can become complex. Regular audits of roles and permissions are necessary to prevent redundancy.
- Overhead in Role Management: Dynamically changing business requirements may necessitate frequent updates to the roles and permissions matrix. Automating role updates through admin dashboards can alleviate this burden.
- Security Risks: Misconfigured permissions or loopholes in role assignment can lead to unauthorized access. Comprehensive testing and code reviews are essential to mitigate these risks.
A full stack developer course often includes best practices for addressing these challenges, equipping developers with the skills needed to implement RBAC effectively.
Enhancing RBAC with Advanced Features
Modern applications often extend RBAC to incorporate advanced features such as:
- Hierarchical Roles: Allow roles to inherit permissions from parent roles, reducing redundancy. For example, an admin role could inherit all permissions from an editor role.
- Dynamic Roles: Enable roles to be dynamically assigned based on user behavior or context, such as location or device type.
- Audit Trails: Implement logging mechanisms to track access and permission changes, improving accountability and compliance.
These features add complexity to RBAC systems, making them suitable for experienced developers. Aspiring professionals can learn about these advanced implementations in a full stack course in Hyderabad, which offers a comprehensive curriculum tailored to current industry demands.
Conclusion
Role-Based Access Control (RBAC) is a critical component of modern full stack applications, enabling developers to manage user permissions efficiently and securely. From designing a permissions matrix to implementing robust backend and frontend controls, RBAC requires a deep understanding of full stack development principles.
For those seeking to master these skills, enrolling in a developer course provides a structured pathway to becoming proficient in implementing RBAC and other advanced features. Additionally, localized training programs, such as a full stack developer course in Hyderabad, offer hands-on experience in building secure and scalable applications tailored to the needs of today’s dynamic tech landscape.
By investing time in learning and applying RBAC techniques, developers can create applications that not only meet functional requirements but also uphold the highest standards of security and user management.
Contact Us:
Name: ExcelR – Full Stack Developer Course in Hyderabad
Address: Unispace Building, 4th-floor Plot No.47 48,49, 2, Street Number 1, Patrika Nagar, Madhapur, Hyderabad, Telangana 500081
Phone: 087924 83183